AN ENSEMBLE OF TOKENIZATION, AUTOENCODER AND TEMPORAL CONVOLUTIONAL NETWORK FOR SQL INJECTION DETECTION.
DOI:
https://doi.org/10.60787/tnamp.v23.625Keywords:
SQL Injection, Deep Learning, Temporal Convolutional Network, Autoencoder, CybersecurityAbstract
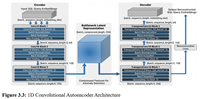
SQL Injection (SQLi) attacks remain a critical cybersecurity threat, with traditional detection methods struggling against novel attack patterns. This study proposes a hybrid deep learning architecture combining SQL-aware tokenization, a 1D Convolutional Autoencoder (1D-CAE), and a Temporal Convolutional Network (TCN) for robust SQLi detection. The framework leverages the autoencoder for unsupervised anomaly detection and the TCN for temporal sequence modeling. Evaluated on 30,918 SQL queries, the proposed ensemble achieved 98.53% accuracy, 92.5% precision, 95.5% recall, and 94.0% F1-score, significantly outperforming Random Forest (87.0% F1-score) and individual model components. The TCN's parallel processing capability enabled 12.3 milliseconds average inference time per query, supporting real-time deployment. The fusion of anomaly-based and sequence-based deep learning provides an efficient, scalable defense against both known and zero-day SQLi attacks.
Downloads
References
Bai, S., Kolter, J. Z., & Koltun, V. (2018). An empirical evaluation of generic convolutional and recurrent networks for sequence modeling. arXiv preprint arXiv:1803.01271. <https://doi.org/10.48550/arXiv.1803.01271>
Chawla, N. V., Bowyer, K. W., Hall, L. O., & Kegelmeyer, W. P. (2002). SMOTE: Synthetic minority over-sampling technique. Journal of Artificial Intelligence Research, 16, 321–357. <https://doi.org/10.1613/jair.953>
Fortinet. (2023). What is SQL injection (SQLi) and how to prevent it? Fortinet. Retrieved from <https://www.fortinet.com/resources/cyberglossary/sql-injection>
Ketema, B., & Sharma, D. (2022). A survey on deep learning-based SQL injection detection. Journal of Cybersecurity and Privacy, 2(3), 524–543. <https://doi.org/10.3390/jcp2030027>
Nanang, A. (2023). A comprehensive review of blind SQL injection attacks and mitigation techniques. International Journal of Computer Science and Network Security, 23(1), 1–10.
Naser, M., Al-Rousan, T., & Al-Shargabi, B. (2022). A comprehensive survey on SQL injection attacks: A systematic literature review. IEEE Access, 10, 84999–85021. <https://doi.org/10.1109/ACCESS.2022.3197533>
Neel, S., & Sharma, T. (2023). A systematic review of deep learning techniques for SQL injection detection. Journal of King Saud University - Computer and Information Sciences, 35(1), 23–37. <https://doi.org/10.1016/j.jksuci.2022.11.015>
OWASP. (2024). OWASP Top 10:2024. Open Web Application Security Project. Retrieved from <https://owasp.org/www-project-top-ten/>
Shahriar, H., & Zulkernine, M. (2023). A survey on SQL injection attacks: Vulnerabilities and countermeasures. ACM Computing Surveys, 55(1), 1–38. <https://doi.org/10.1145/3507909>
Vinayakumar, R., Soman, K. P., & Poornachandran, P. (2017). Applying convolutional neural network for network intrusion detection. In 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI) (pp. 1222-1228). IEEE. <https://doi.org/10.1109/ICACCI.2017.812322115.8>
Downloads
Published
Issue
Section
License
Copyright (c) 2025 The Transactions of the Nigerian Association of Mathematical Physics

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.