Enhanced Model For Intrusion Detection In A Cloud Environment
DOI:
https://doi.org/10.60787/jnamp.vol69no1.468Keywords:
Intrusion, Detection, Internet, Machine learning, ComputingAbstract
The cyber security industry is rapidly growing due to the expanding size of networks, which increases the attack surface for hackers. As cyber threats become more sophisticated, defenses must also advance. This research employs the Zhang 2019 model, utilizing a Deep Generative Neural Network (DGNN) for adversarial learning. DGNN comprises two components: G-net, which generates malicious inputs (intrusion samples), and D-net, which identifies these from real inputs. Over time, G-net produces more sophisticated malicious inputs as D-net improves its detection. The developed model monitors and analyzes data in a cloud computing environment, detecting intrusions from both external and internal users using Support Vector Machine and Bayesian network techniques. Data is collected, pre-processed, normalized, and classified into normal (ND) or intrusion data (ID). The normal data is treated as regular network requests, while intrusion data undergoes further processing before entering the deep learning training model.
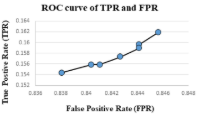
In the testing phase, a test data was obtained with the use of data packet receiver and classification of the intrusions as True positive, false positive, true negative and false negative. Each frame was analyzed for true positive and true negative, the result gotten from the classification and analyses of the intrusions were used to compare and evaluate the performance of the enhanced intrusion detection model to ascertain if it was better than the Zhang model. The enhanced model effectively predicts and detects intrusion attacks and unauthorized users, providing valuable information about malicious network traffic and alerting security personnel to potential invasions.
Downloads
References
Alessandri.D. (2000): Using rule-based activity descriptions to evaluate intrusion-detection systems. In RAID2000, H. Debar, L. Me, and S. F. Wu, Eds. Springer-Verlag, New York, NY, 183–196.
Adel Binbusayyis, Haya Alaskar, Thavavel Vaiyapuri, M. Dinesh. (2022)
An investigation and comparison of ML approaches for intrusion detection in IoMT network J. Supercomput., 78, pp. 17403-17422
Ayesha S.Dina, Manivannan D. (2021) Intrusion detection based on Machine Learning techniques in computer networks. Elsevier (iot) Volume 16, December 2021, 100462
Kathryn-Ann Tait, Jan Sher Khan, Fehaid Alqahtani , Awais Aziz Shah , Fadia Ali Khan, Mujeeb Ur Rehman , Wadii Boulila, Jawad Ahmad1(2021) Intrusion Detection using Machine Learning Techniques: An Experimental Comparison.(Journal of information Security and Applications, 2021)
Stephen Kahara Wanjau, Geoffrey Mariga Wambugu, Aaron Mogeni Oirere (2022) Network Intrusion Detection Systems: A Systematic Literature Review of Hybrid Deep Learning Approaches. International Journal of Emerging Science and Engineering (IJESE) ISSN: 2319–6378 (Online), Volume-10 Issue-7, June 2022
Abdallah.E.Emad, Wafa Eleisah, Ahmed Fawzi Otoom. (2022) Intrusion Detection Systems using Supervised Machine Learning Techniques: A survey. Procedia computer science (volume 201, 2022, pages 205-212. Elsevier.
Dayanand Ingle1 and Dr. B.B. Meshram (2012): Hybrid Analysis and Design Model for Building Web Information System. IJCSI International Journal of Computer Science Issues, Vol. 9, Issue 4, No 3, July 2012 ISSN (Online): 1694-0814.www.IJCSI.org
Elike Hodo, Xavier Bellekens, Andrew Hamilton, Christos Tachtatzis, Robert Atkinson. (2017) Shallow and deep networks intrusion detection system: a taxonomy and survey, arXiv preprint arXiv: 1701.02145 (2017).1-43.
Gupta. S, Horrow. S and Sardana. A. (2012):“A Hybrid Intrusion Detection Architecture for Defense against DDoS Attacks in Cloud Environment,” Contemporary Computing Communications in Computer and Information Science, Vol. 306, ISBN: 978-3-642-32129-0, pp. 498-499.
Gómez J., Gil C., Padilla N., Baños R. and Jiménez C. (2009): “Design of a snort-based hybrid intrusion detection system,” in Distributed Computing, Artificial Intelligence, Bioinformatics, Soft Computing, and Ambient Assisted Living, pp. 515–522, Springer, Berlin, Germany, View at Google Scholar.
Hwang, K., Cai. M, Chen Y., Member. S, and Qin. M (2007): “Hybrid Intrusion Detection with Weighted Signature Generation over Anomalous Internet Episodes”, IEEE Transactions on Dependable and Secure Computing, 4(1), pp. 1-15.
Hisham A. Kholidy, Baiardi F. (2012): CIDS: A framework for intrusion detection in cloud systems. Proceedings of 9th IEEE International Conference on Information Technology-New Generations.p. 379–85.
Internet-Computer-Security (2011): IPS (Intrusion Prevention System) and IDS (Intrusion Detection Systems) http://www.internet-computer-security.com/Firewall/IPS.htmlInternational Journal of Network Security & Its Applications (IJNSA), Vol.4, No.2, March 2012 113.
Kleber and schulter (2010): “Intrusion Detection for Grid and Cloud computing”, IEEE Journal: IT Professional.
McHugh J., Allen, J., A. Christie, W. Fithen, J. Pickel, E. Stoner. (2000): State of the practice of intrusion detection technologies. Technical Report CMU/SEI-99-TR-028 ESC-99- 028, Pittsburgh, PA.
Sang-Jun Han and Sung-Bae Cho. (2003): Combining Multiple Host-Based Detectors Using Decision Tree, Australian Joint Artificial Intelligence Conference, (AUSAI).
Tupakula U, Varadharaja V, Akku N. (2011): Intrusion detection techniques for infrastructure as a service cloud. Proceedings of 9th IEEE International Conference on Dependable, Autonomic and Secure Computing. p. 744–51.
Zamani. M and Movahedi. M. (2013) "Machine learning techniques for intrusion detection", arXiv: 1312.2177.
Zeeshan Ahmad, AdnanShahid Khan, Wai hiang Cheah, Johari Abdullah, Farhan Ahmad. (2021) Network intrusion detection system: a systeatic study of ML and DL approaches
Transactions on Emerging Telecommunications Technologies, 32, Article e4150
Zhang He, Xingrui Yu, Peng Ren, Chumbo Luo, Geyong Min (2019). Deep Adversial learning in intrusion detection. A data Augmentation Ehanced Framework.ArXiv: 1901.07949v3 [CS.CR]
Downloads
Published
Issue
Section
License
Copyright (c) 2025 The Journals of the Nigerian Association of Mathematical Physics

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.