INVESTIGATING TRUSTED ROUTING MECHANISM ON A FULL-MESHED TELECOMMUNICATION NETWORK MODEL
Keywords:
network agent, trusted node, node monitoring, telecommunication network, routing mechanism, Trusted routingAbstract
The article is on the study of the properties of the trusted routing mechanism via simulation experiments of a fully-meshed telecommunication network model. The description of the model, the experimental results and their interpretations are given.
Downloads
References
M. V. Buinevich, O. A. Tiamiyu, "Software Architecture of Trusted Routing Management System in Global Telecommunication Networks (Программная архитектура системы управления доверенной маршрутизацией в глобальных телекоммуникационных сетях)," Information and Communication («Информатизация и связь»), vol. 3, pp. 35-38, 2014.
O. A. Tiamiyu, "An Overview of Modern Telecommunication Networks Security Challenges. National Security and Strategic Planning (Национальнная Безопасность и Стратетическое Планирование)," National Security and Strategic Planning (Национальнная Безопасность и Стратетическое Планирование), vol. 2, no. 2, pp. 37-43, 2013.
O. A. Tiamiyu, D. A. Olaode, F. Ahmamush, "Issues on the international standardization in the field of information security," Science Journal VESTNIK ENGEC: Technical Science Series (Научный Журнал «Вестник Инжекона: Серия Технические Науки»), vol. 67, no. 8, p. 100−102, 2012.
V. M. Zima, A. A. Moldovian, N. A. Moldovian, Безопасность глобальных сетевых технологий, СПб: ХВ-Петербург, 2000.
O. A. Tiamiyu, "Trusted Routing Device in Telecommunication Networks (Устройство Доверенной Маршрутизации в
Телекоммуникационных Сетях)". Russia Patent RU Patent № 150245, 10 2 2015.
O. A. Tiamiyu, "Trusted routing vs. MPLS: Data security, QoS and network scalability," Electronic Science Journal «Information Technologies and Telecommunications» (Электронный Научный Журнал «Информационные Технологии и Телекоммуникации»), vol. 3, p. 4−13, 2013.
O. A. Tiamiyu, "Comparative Analysis of Imitation Modeling Software Supporting Trusted Routing (Сравнительный Анализ Средств Имитационного Моделирования ТКС, Поддерживающих Доверенную Марщрутизацию)," in Topical issues on problems of information security: collection of scientific articles (Актуальные Проблемы Информационной Безопасности,
Сборник Научных Трудов), 2012, p. 49−53. Open Systems Interconnection. Basic Reference Model Part, 2.
O. A. Tiamiyu, "Analysis of IP Routing Protocols for Trusted Routing in the Global Data Networks.," Science Journal VESTNIK ENGEC: Technical Science Series (Научный Журнал «Вестник Инжекона: Серия Технические Науки»), vol. 59, no. 8, p. 157−160, 2012.
H. Chuanhe, Y. Cheng, Y. Ling, H. Xhou, "Trusted dynamic source routing protocol," in International Conference on Wireless Communications, Networking and Mobile Computing, 2007.
T. Ghosh, N. Pissinou, S. K. Makki, "Towards designing a trusted routing solution in mobile ad hoc networks," Mobile Networks and Applications, vol. 10, no. 6, pp. 985-995, 2005.
A. Datta, C. Mcdonald, A. Pirzada, "Trusted routing in ad-hoc networks using pheromone trails.," in 2004 Congress on Evolutionary Computation, 2004.
K. K. Somasundaram, J. Baras, "Path Optimization and Trusted Routing in MANET: An Interplay Between Ordered Semirings.," in International Conference on Computer Science and Information Technology, Berlin, 2011.
K. YANG, J. I. MA, C. YANG, "Trusted routing based on DS evidence theory in wireless mesh network," Journal on Communications, vol. 32, no. 5, p. 89, 2011.
Q. Wu, Q. Liu, Z. Zhiming, "A trusted routing protocol based on GeoDTN+ Nav in VANET," China Communications, vol. 11, no. 14, pp. 166-174, 2014.
O. A. Tiamiyu, "Recommendations for improving the implementation of trusted routing mechanism (РЕКОМЕНДАЦИИ ПО
СОВЕРШЕНСТВОВАНИЮ РЕАЛИЗАЦИИ МЕХАНИЗМА ДОВЕРЕННОЙ МАРШРУТИЗАЦИИ)," Electronic Scientific Journal «Information Technologies and Telecommunications» (Электронный Научный Журнал «Информационные Технологии и Телекоммуникации»), vol. 1, p. 413−417, 2015.
T. Chen, O. Mehani, R. Boreli, "Trusted routing for VANET," in 2009 9th International Conference on Intelligent Transport Systems Telecommunications, 2009.
S. S. Hazra , "Trusted routing in AODV protocol against wormhole attack," in Future Information Technology, Application, and Service, Springer, 2012, pp. 259-269.
Z. A. Zardari, J. H. Muhammad, S. Pathan, S. Qureshi, N. Zhu, "Detection and prevention of Jellyfish attacks using kNN algorithm and trusted routing scheme in MANET," International Journal of Network Security, vol. 23, no. 1, pp. 77-87, 2021.
Z. Qin, Z. Jia, X. Chen, "Fuzzy dynamic programming based trusted routing decision in mobile ad hoc networks," in Fifth IEEE International Symposium on Embedded Computing, 2008.
S. Peng, W. Jia, G. Wang, J. Wu, N. Guo, "Trusted routing based on dynamic trust mechanism in mobile ad-hoc networks," IEICE TRANSACTIONS on Information and Systems, vol. 93, no. 3, pp. 510-417, 2010.
O. A. Tiamiyu, "Trusted Routing vs. VPN for Secured Data Transfer over IP-Networks/Internet," in 2nd International Scientific and Practical Conference «Fundamental and applied research in the modern world» (Материалы II Международной Научно-практической Конференции «Фундаментальные и Прикладные Исследования в Современной Мире»), 2013.
O. A. Tiamiyu, "Selection and Rationale of Algorithm for Network Topology Determination in the Interest of Trusted Routing," Electronic Science Journal «Information Technologies and Telecommunications» (Электронный Научный Журнал «Информационные Технологии и Телекоммуникации»), vol. 1, pp. 54-66, 2014.
S. Vasileva, A. Kulchiar, "Options of GPSS World for integrated demonstration models in the educational process," in 2014 Science and Information Conference, 2014.
В. Д. Боев, Моделирование систем. Инструментальные средства GPSS WORLD, Петербург: БХВ-Петербург, 2004.
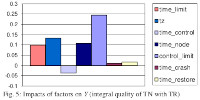
Downloads
Published
Issue
Section
License
Copyright (c) 2024 The Journals of the Nigerian Association of Mathematical Physics

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.